
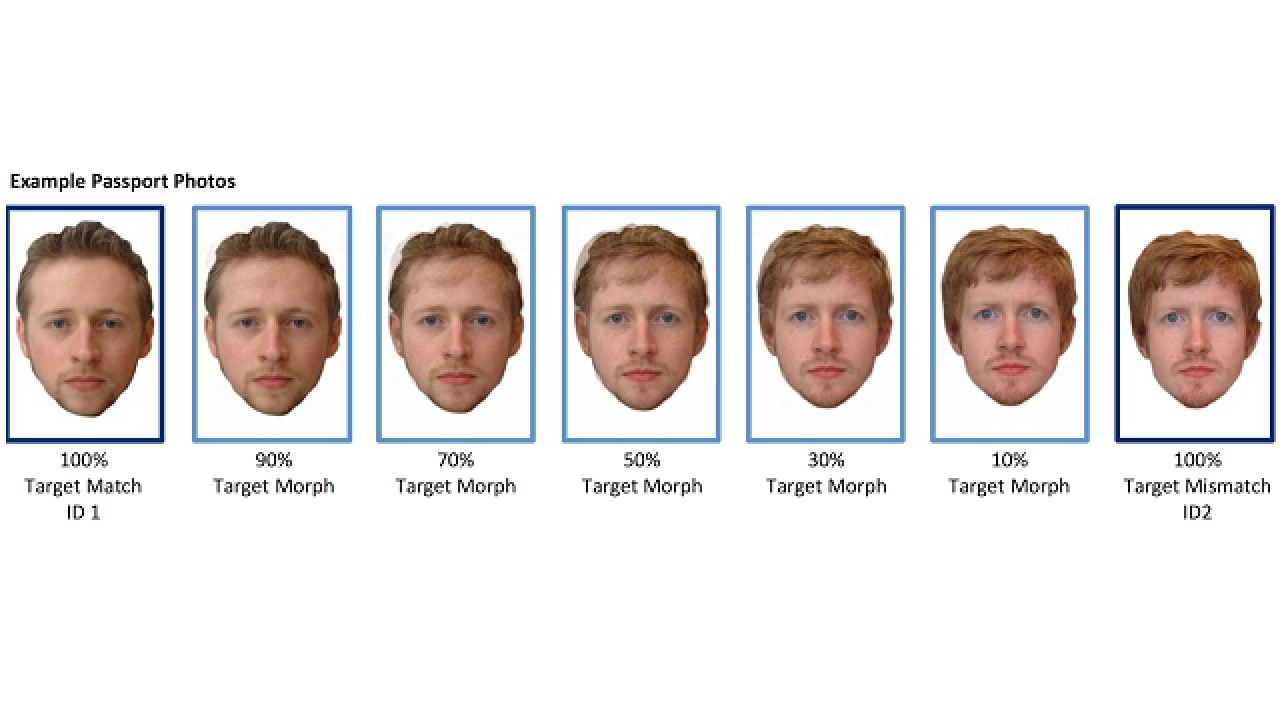
An example of a morph continuum, changing a female face (original and... | Download Scientific Diagram

Applied Sciences | Free Full-Text | Face Morphing, a Modern Threat to Border Security: Recent Advances and Open Challenges
Medium Face morphing Comparison: (a) MorphThing result, (b) Proposed... | Download Scientific Diagram

Applied Sciences | Free Full-Text | A Comprehensive Review of Face Morph Generation and Detection of Fraudulent Identities





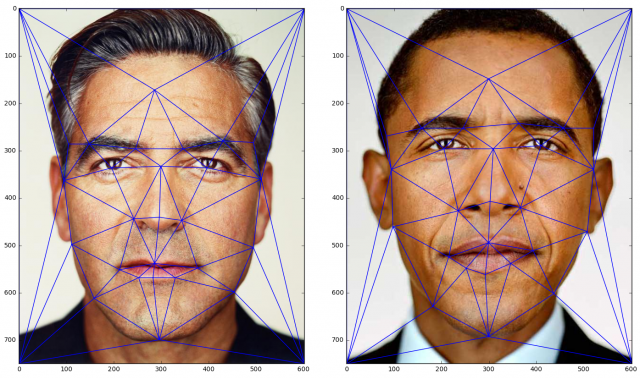
![PDF] Face Recognition Systems Under Morphing Attacks: A Survey | Semantic Scholar PDF] Face Recognition Systems Under Morphing Attacks: A Survey | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/680405eab6adfdeab5aba0e182b6210e6dbe9406/1-Figure1-1.png)




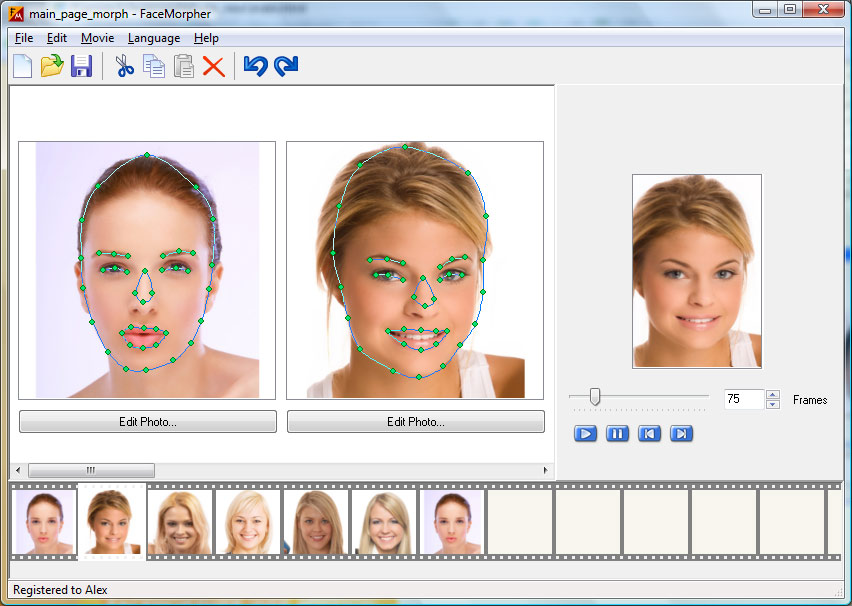


.webp)

